The DM That Started It All 💼
There I was, scrolling through “Threads city” office edition like any other day, checking the latest news, drama, and farewells.
Then this chump slides into my DMs:
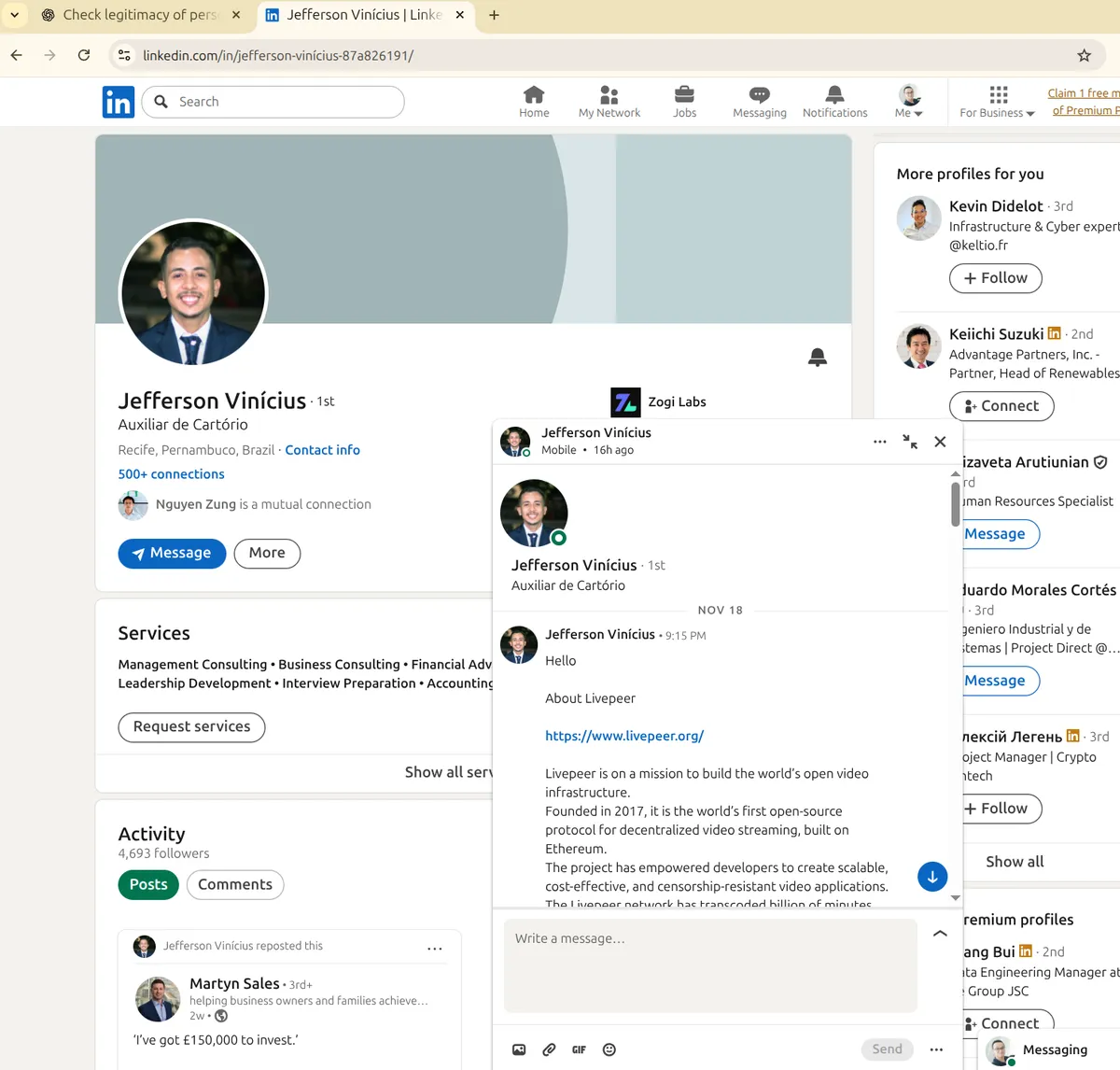
Jefferson Vinícius - Brazilian profile, zero connection to Livepeer anywhere. Probably stole someone’s avatar, but still looks like a clown:
“Hey! Livepeer is offering a monthly salary of 15–20k USD with flexible working hours and fully remote. Are you interested?”
Had to read that twice.
$15-20k. Per month. Remote. Work whenever you want.

I knew Livepeer - legit crypto video infrastructure company. Almost bought their token during one of those FOMO bull runs.
But… $20k/month?! That’s FAANG guru money, and they’re recruiting ME, some random dude named HoangYell? That’s like inviting a local league player to carry Liverpool!
Smells like BS. But hey, those self-help books always say “seize opportunities.” Maybe the universe is blessing me? Or maybe crypto companies just throw money around? Let’s play along. Sometimes even a blind dog catches a bone…
Red Flag #1: The Time Zone Fiasco ⏰
He says there’s a technical assessment. Cool, I’ve done a hundred of these. I schedule 2:00 UTC on Saturday.
He agrees instantly. No “let me check my calendar.” Just “OK!”
His profile says Brazil. Brazil is UTC-3. Quick math: 2:00 UTC = 11 PM Friday night over there.
Either this guy’s the most dedicated recruiter in human history, or… he ain’t in Brazil.
I even asked ChatGPT if the profile looked legit. It gave some wishy-washy answer. Basically useless.

Red Flag #2: Vanished Without a Trace 👻
Saturday arrives. I message him at 2:00 UTC: “Ready to go!”
Silence.
Wait. Grab coffee. Pee & poop. Come back. Still nothing.
12 hours later, he drops a link like nothing happened:
“Here’s the assessment:
https://bitbucket.org/livepeer-labs/technical-assessment”
No apology. Nothing. Just casually drops the link.
Recruiting for a $20k/month position with this level of professionalism… 🤡
Pro tip: Scammers are terrible at pretending to be normal humans.
Red Flag #3: Why Bitbucket Though? 🎣
Livepeer’s real repos? github.com/livepeer - over 200 of them, all on GitHub.
But their “technical assessment”? Hosted on some random Bitbucket account. Yeah, sure, totally legit. 🙄
⚠️ WARNING
This repo contains actual malware. Don’t run it unless you enjoy letting strangers party in your machine.
(Original repo got nuked. Here’s my fork if you wanna see the crime scene.)

Red Flag #4: “Just Clone and Run It” 🚨
He told me to pull the repo and run it locally for the assessment.
I’ve done tons of coding challenges. Never has a legit company said “just download our mystery code and execute it, trust me bro.”
Real companies use:
- Simple task descriptions: “Build X from scratch”
- Online IDEs (HackerRank, CodeSignal)
- Their own platforms
Nobody says “just run this random project on your machine, trust me bro!”
That’s not a test. That’s a delivery mechanism for sketchy stuff.
Red Flag #5: The Assessment Makes Zero Sense 🎭
The task:
“When you stop recording, display the canvas drawing as a video.”
Neat frontend challenge. One problem: my entire profile screams backend developer. APIs, databases, system design. CV? Backend. Projects? Backend.
They didn’t read anything. They just needed a warm body to run npm install.
Seriously, are these people stupid? Giving a frontend task to a backend dev?

I had two choices:
- Run it on my main machine like an idiot
- Be suspicious right now
I chose to be suspicious. Fired up my sandbox laptop - the one with cracked games, shady downloads, and literally nothing I care about. If they wanna steal something, they can have my CS 1.6 saves from 2008.
Red Flag #6: WTF Is execp Doing Here? 🔍
First thing I did: check package.json.
A simple canvas app should have basic dependencies. But this one had:
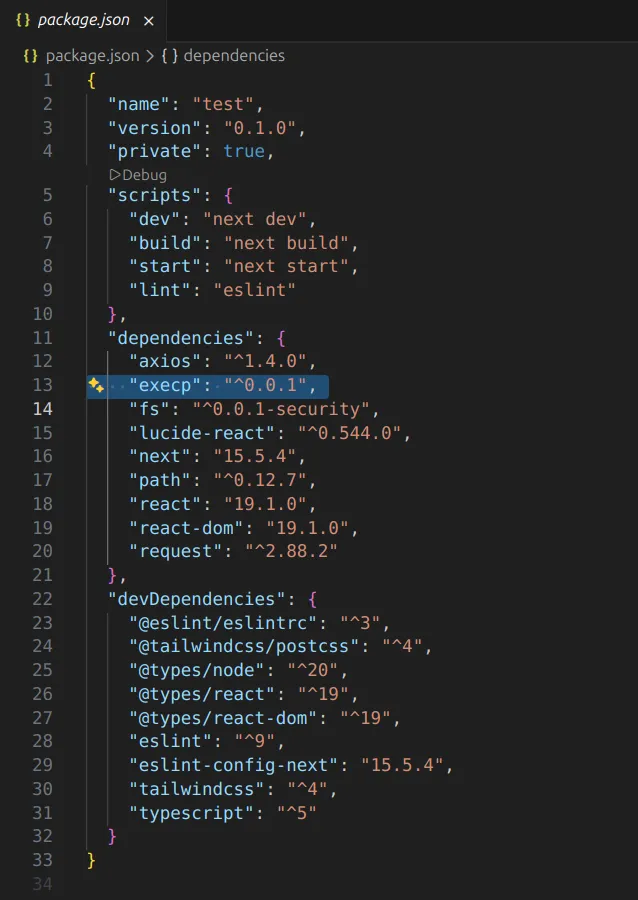
execp - a module for executing system commands.
In. A. Canvas. Drawing. App.
Why would a basic frontend app need to run system commands?
The stench is getting stronger.
AI Caught It Instantly 🤖
I asked Google’s new shiny assistant: “tell me what this does.”
Response:
“Yeah, this is malware. Here’s what it’s doing…”
Not “interesting project.” Not “looks normal.” Straight up: malware.
The Reveal: Hundreds of Hidden Lines 🧬
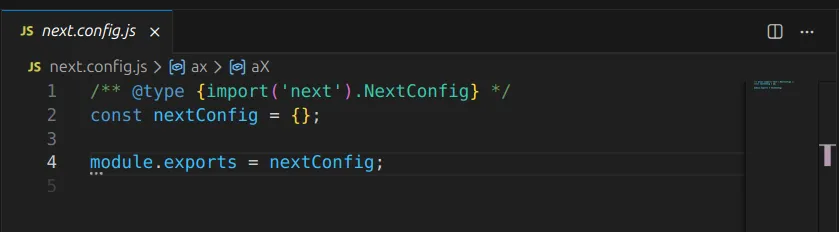
Opened next.config.js. Looked innocent:
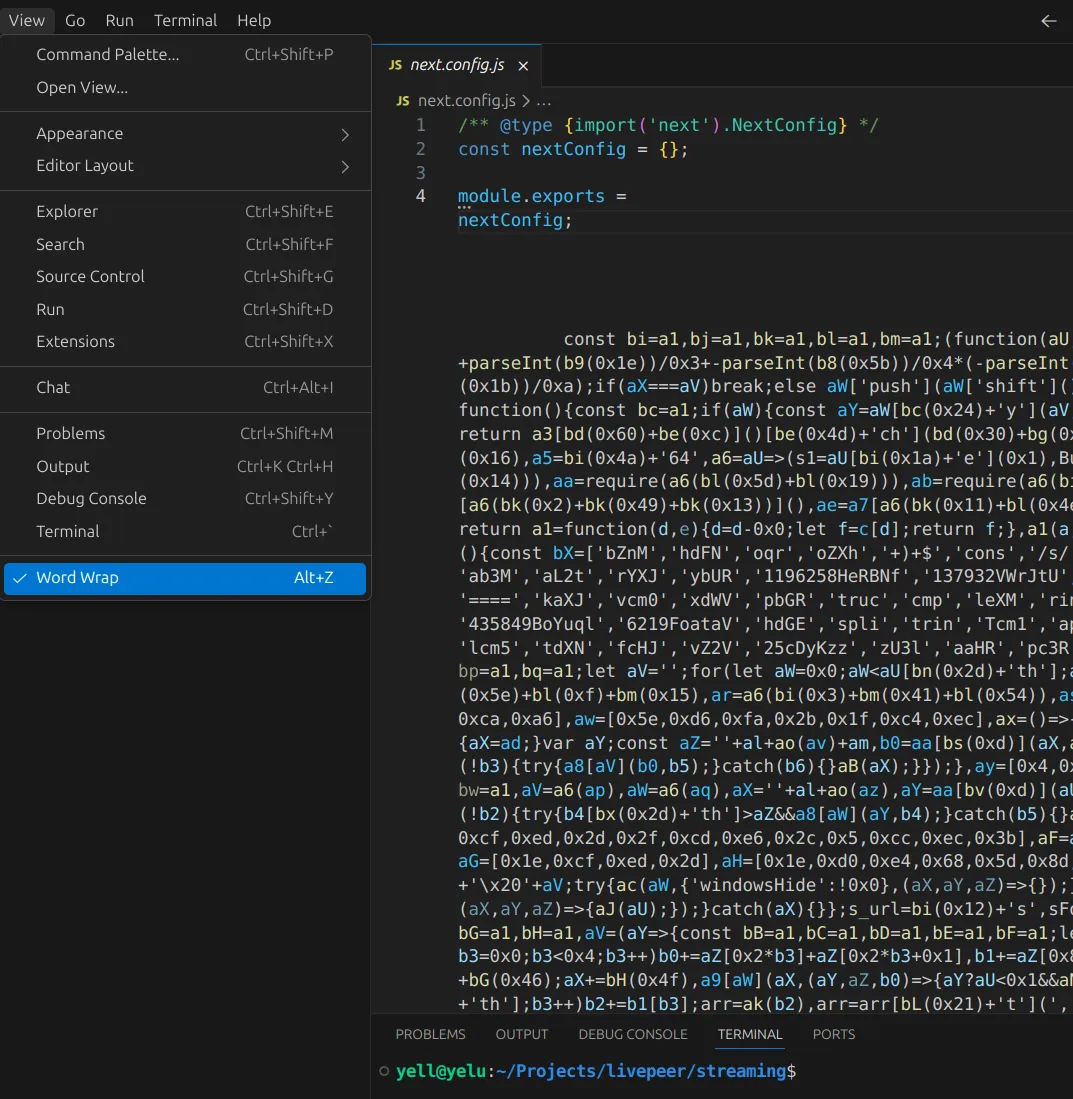
Then I turned on word wrap.
Holy. Shit.
What looked like 5 lines was actually hundreds of obfuscated JavaScript crammed onto single lines. Classic trick.
After deobfuscation, here’s what the malware does:
- Phones home to
http://45.43.11.248:1244 - Fingerprints victim machine (username, hostname)
- Downloads next-stage malware
- Hides it in
~/.vscode/to look legit - Executes the payload
- Retries every 10 minutes if it fails
| |
The repo was just step one. A delivery boy. The real damage would come from whatever gets downloaded next.
Welp, I get it now. There’s no gold falling from the sky. Just bird shit and rain.
I Trolled Him Back a Little 😈
I told Jefferson I was done, asked if I should submit a PR.
His response? He didn’t care about the code at all. He wanted a video of the app running - proof that I’d executed his package.
You think you can scam me? Bitch, nice try, idiot. 😏
I didn’t send anything. Went silent.
I was planning to send him this blog post to “evaluate my assessment.” Shame he disappeared from LinkedIn before I could finish writing. What a loss. 🤷

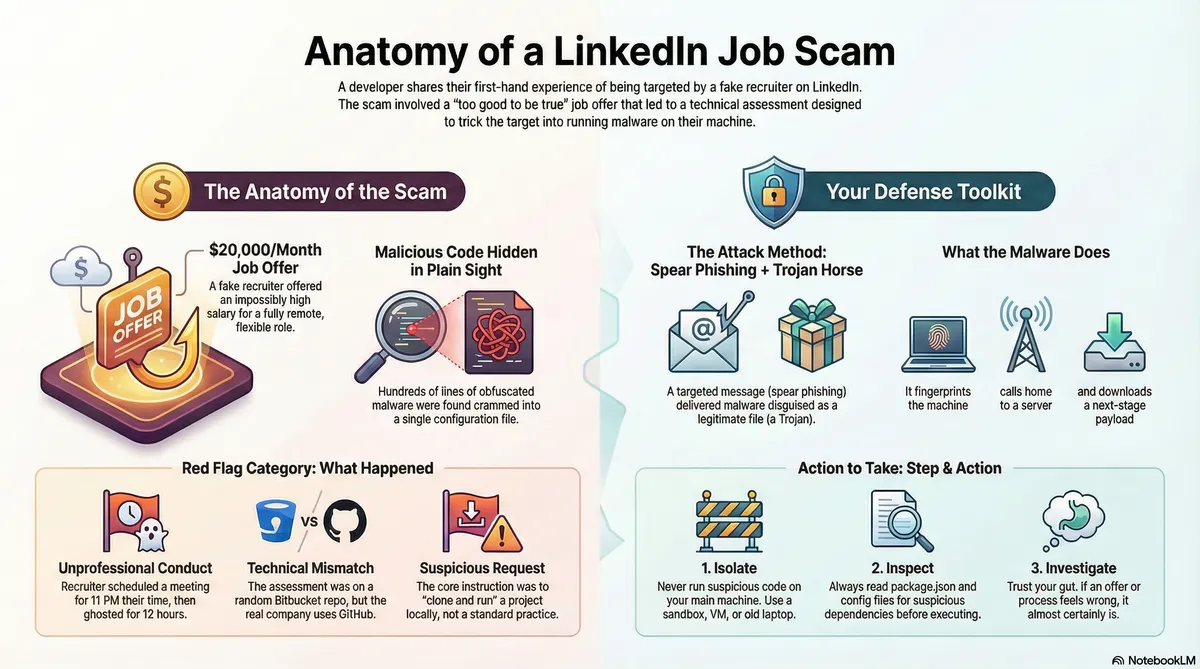
TL;DR: The Red Flags 🚩
| # | Red Flag | Why It’s Sus |
|---|---|---|
| 1 | Sloppy timing | Agrees to 11 PM Saturday his timezone, then ghosts for 12 hours |
| 2 | Hosting mismatch | Real company uses GitHub, “assessment” on random Bitbucket |
| 3 | “Clone and run it” | Nobody legit asks you to execute mystery code |
| 4 | Wrong assessment type | Frontend task for a backend dev? Nonsense |
| 5 | execp in a canvas app | System commands in a drawing demo? |
| 6 | Obfuscated config | Hundreds of hidden lines in next.config.js |
What’s This Attack Called? 🎓
Two classic techniques, one combo attack:
1. Spear Phishing 🎯
Regular phishing = spam 1,000 random people with “you won a prize” emails.
Spear phishing = targeted. This dude looked at my profile, saw “developer,” and crafted a personalized message (Livepeer, remote, $20k). It’s phishing with aim.
2. Trojan Horse 🐴
Remember the Greeks hiding soldiers inside a wooden horse as a “gift”?
This “Technical Assessment” repo is the Trojan. Looks like a normal coding challenge. Actually contains malware waiting to execute the moment you run npm install.
Quick cheat sheet:
| Term | What It Is | Spreads By Itself? |
|---|---|---|
| Malware | Umbrella term for all bad software | — |
| Virus | Malware that self-replicates | ✅ Yes |
| Trojan | Malware disguised as legit software | ❌ No, YOU run it |

How to Not Get Owned 🛡️
- Use a sandbox. VM, old laptop, whatever. Never run sus code on your main machine.
- Read
package.jsonfirst. Takes 30 seconds. Could save your ass. - Trust your gut. If it feels wrong, it probably is.
- No legit $20k offer dies just because you refused to run some shady Bitbucket repo.
What Actually Saved Me
No elite hacking skills here. Just:
- 🧠 Paranoia (healthy amount)
- 💻 A sandbox laptop I don’t care about
- ⏱️ 30 seconds reading dependencies
- 🤖 AI to decode the obfuscated mess
- 🚶 Staying alert to too-good-to-be-true bait
Remember: If it sounds too good to be true, it’s 99% a scam. Don’t be greedy.